الان اینجا هستید:

دوره SANS SEC504
- نوع دوره: حضوری و آنلاین
- سطح دوره: مبتدی
- مدت دوره: 40 ساعت
- پیش نیاز:
- تقویم برگزاری دوره
ناموجود
در حال حاضر کلاسی برای این دوره موجود نیست، اما شما میتوانید درخواست خود را برای برگزاری مجدد این دوره از فرم زیر برای ما ارسال کنید.
"(اجباری)" indicates required fields
- چرا کندو؟

ضبط تصویری

دسترسی ریموت

ضمانت شغل
- معرفی این دوره
امروزه در دنیای IT ، حوزه امنیت بسیار مهم و حیاتی است. در دوره SEC504 که توسط شرکت SANS ارائه می شود تکنیک ها و ابزارهای نفوذ به شبکه را به افراد آموزش می دهد. این مباحث مربوط به پاسخگویی به حوادث (Incident Responses)و تست نفوذ(Penteration Testing) میباشد SANS مخفف SysAdmin, Audit, Network and Security است.
- مدرک پایان دوره
- کندو معتبرترین آموزشگاه IT ایران است که بیشترین فارغالتحصیلان را دارد.
- بسیاری از مدیران صنعت IT ایران در آموزشگاه کندو دوره دیدهاند.
- بسیاری از فارغ التحصیلان آموزشگاه کندو خارج از ایران مشغول به کار شدهاند.
- مدرک کندو قابلیت ترجمه و استفاده برای امور مهاجرتی را نیز دارد.
- مدارک دورههای حضوری و آنلاین هیچ تفاوتی با هم ندارند.
نمونه مدارک:
- اهداف و دستاوردها
· شبکه و گزارش
· بهترین روشها برای پاسخدهی موثر به رویداد
· فرآیندهای تحقیقات سایبری با استفاده از تجزیه و تحلیل زنده
· چگونه مهاجمان از سیستم های ابری علیه سازمان ها استفاده می کنند
· تکنیک های مهاجم برای فرار از ابزارهای تشخیص نقطه پایانی
- امکانات و فضای آموزشگاه
- لابراتوار تجهیز شده ۲۴ ساعته و رایگان
- سیستم و اینترنت پرسرعت + فیلترشکن
- ضبط محتوای کلاس و دسترسی دائم به آن
- کافه + امکانات پذیرایی بین کلاس
- فوتبال دستی و پینگ پنگ
- فضای سبز تجهیز شده
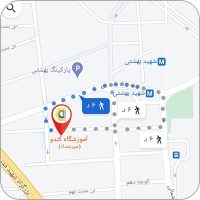
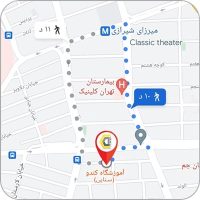
دو آموزشگاه در تهران:
- ساختمان میرعماد: خیابان مطهری، خیابان میرعماد، کوچه جنتی ۱۳، پلاک ۳۰ (فاصله تا متروی بهشتی ۵ دقیقه پیاده)
- ساختمان سنایی: خیابان سنایی، تقاطع خیابان مطهری، کوچه ۲۱، پلاک ۲ (فاصله تا متروی میرزای شیرازی ۱۰ دقیقه پیاده و ایستگاه BRT ولیعصر ۱۰ دقیقه)
مسیریابی از روی گوگلمپ:
- سرفصل های SANS SEC504
SECTION 1: Incident Response and Cyber Investigations
SECTION 2: Recon, Scanning, and Enumeration Attacks
SECTION 3: Password and Access Attacks
SECTION 4: Public-Facing and Drive-By Attacks
SECTION 5: Evasion and Post-Exploitation Attacks
SECTION 6: Capture-the-Flag Event
- داشجویان کندو مشغول به کار شدن در...

فناوری اطلاعات شاتل

شرکت عالیفرد سنایچ

بانک پاسارگاد

بانک ملت

شرکت ارتباطات آسیاتک

پیشگامان توسعه ارتباطات

ایران خودرو

بانک خاورمیانه

ماموت خودرو

پارس خودرو
- اساتید این دوره
- نمونه تدریس
- نظرات شما