الان اینجا هستید:

دوره CCNP Security SCOR 350-701
- نوع دوره: حضوری و آنلاین
- تقویم برگزاری دوره
۲۰٪ تخفیف دوره آنلاین
زمانی دیگر؟
اگر زمان برگزاری این دوره برای شما مناسب نیست، زمان موردنظر خودتون رو از ما درخواست کنید
- چرا کندو؟

ضبط تصویری

دسترسی ریموت

ضمانت شغل
- معرفی این دوره
دوره The Implementing and Operating Cisco Security Core Technologies (SCOR) v1.0 به شما کمک می کند تا برای Cisco® CCNP® Security and CCIE® Security و برای نقش های امنیتی در سطح ارشد آماده شوید. در این دوره ، شما مهارت ها و فن آوری های لازم برای پیادهسازی راه حل های اصلی امنیتی سیسکو را برای محافظت از تهدید پیشرفته در برابر حملات امنیت سایبری تسلط خواهید یافت. شما امنیت شبکه ، ابر و محتوا ، حفاظت از نقطه پایانی، دسترسی ایمن به شبکه ، قابلیت مشاهده و اجرا را یاد خواهید گرفت. شما با استفاده از فایروال Cisco Firepower® Next-Generation Firewall و Cisco Adaptive Security Appliance (ASA) Firewall تجربه عملی عملی خواهید داشت. پیکربندی سیاست های کنترل دسترسی ، خط مشی های نامه و احراز هویت 802.1X. و بیشتر. شما در مورد ویژگی های شناسایی تهدید Cisco Stealthwatch® Enterprise و Cisco Stealthwatch Cloud تمرین مقدماتی خواهید داشت.
- مدرک پایان دوره
- کندو معتبرترین آموزشگاه IT ایران است که بیشترین فارغالتحصیلان را دارد.
- بسیاری از مدیران صنعت IT ایران در آموزشگاه کندو دوره دیدهاند.
- بسیاری از فارغ التحصیلان آموزشگاه کندو خارج از ایران مشغول به کار شدهاند.
- مدرک کندو قابلیت ترجمه و استفاده برای امور مهاجرتی را نیز دارد.
- مدارک دورههای حضوری و آنلاین هیچ تفاوتی با هم ندارند.
نمونه مدارک:
- اهداف و دستاوردها
SCOR- v1.0 (350-701)
- مفاهیم و استراتژی های امنیت اطلاعات را در داخل شبکه توصیف کنید
- حملات مشترک TCP / IP ، برنامه شبکه و نقطه پایان را توصیف کنید
- شرح دهید که چگونه فن آوری های مختلف امنیتی شبکه برای جلوگیری از حملات با یکدیگر کار می کند
- کنترل دسترسی را در دستگاه های Cisco ASA و Firewower Cisco Firepower نسل بعدی ایجاد کنید
- ویژگی ها و عملکردهای امنیتی محتوای ایمیل اساسی ارائه شده توسط Cisco Email Security Appliance را توصیف و پیاده سازی کنید
- ویژگی ها و عملکردهای امنیتی محتوای وب ارائه شده توسط Cisco Web Security Appliance را توصیف و پیاده سازی کنید
- معرفی VPN ها و توصیف راه حل ها و الگوریتم های رمزنگاری
- راه حل های ارتباطی امن سایت به سایت سیسکو را توصیف کنید و نحوه استقرار سیستم عامل اینترنت سیسکو (Cisco IOS®) VPN های IP-Pro از نقطه به نقطه و VPN نقطه به نقطه IPsec را بر روی آن مستقر کنید. فایروال Cisco ASA و Cisco Firepower نسل بعدی (NGFW)
- امکانات و فضای آموزشگاه
- لابراتوار تجهیز شده ۲۴ ساعته و رایگان
- سیستم و اینترنت پرسرعت + فیلترشکن
- ضبط محتوای کلاس و دسترسی دائم به آن
- کافه + امکانات پذیرایی بین کلاس
- فوتبال دستی و پینگ پنگ
- فضای سبز تجهیز شده
دو آموزشگاه در تهران:
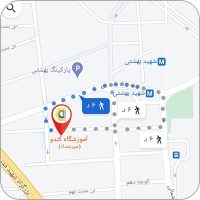
- ساختمان میرعماد: خیابان مطهری، خیابان میرعماد، کوچه جنتی ۱۳، پلاک ۳۰ (فاصله تا متروی بهشتی ۵ دقیقه پیاده)
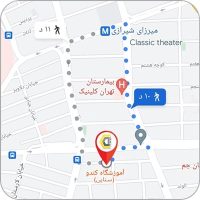
- ساختمان سنایی: خیابان سنایی، تقاطع خیابان مطهری، کوچه ۲۱، پلاک ۲ (فاصله تا متروی میرزای شیرازی ۱۰ دقیقه پیاده و ایستگاه BRT ولیعصر ۱۰ دقیقه)
مسیریابی از روی گوگلمپ:
- سرفصل های CCNP Security SCOR 350-701
- Security Concepts
- Explain common threats against on-premises, hybrid, and cloud environments
- On-premises: viruses, trojans, DoS/DDoS attacks, phishing, rootkits, man-in-themiddle attacks, SQL injection, cross-site scripting, malware
- Cloud: data breaches, insecure APIs, DoS/DDoS, compromised credentials
- Compare common security vulnerabilities such as software bugs, weak and/or hardcoded passwords, OWASP top ten, missing encryption ciphers, buffer overflow, path traversal, cross-site scripting/forgery
- Describe functions of the cryptography components such as hashing, encryption, PKI, SSL, IPsec, NAT-T IPv4 for IPsec, preshared key, and certificate-based authorization
- Compare site-to-site and remote access VPN deployment types and components such as virtual tunnel interfaces, standards-based IPsec, DMVPN, FlexVPN, and Cisco Secure Client including high availability considerations
- Describe security intelligence authoring, sharing, and consumption
- Describe the controls used to protect against phishing and social engineering attacks
- Explain North Bound and South Bound APIs in the SDN architecture
- Explain Cisco DNA Center APIs for network provisioning, optimization, monitoring, and troubleshooting
- Interpret basic Python scripts used to call Cisco Security appliances APIs
- Explain common threats against on-premises, hybrid, and cloud environments
- Network Security
- Compare network security solutions that provide intrusion prevention and firewall capabilities
- Describe deployment models of network security solutions and architectures that provide intrusion prevention and firewall capabilities
- Describe the components, capabilities, and benefits of NetFlow and Flexible NetFlow records
- Configure and verify network infrastructure security methods
- Layer 2 methods (network segmentation using VLANs; Layer 2 and port security; DHCP snooping; Dynamic ARP inspection; storm control; PVLANs to segregate network traffic; and defenses against MAC, ARP, VLAN hopping, STP, and DHCP rogue attacks)
- Device hardening of network infrastructure security devices (control plane, data plane, and management plane)
- Implement segmentation, access control policies, AVC, URL filtering, malware protection, and intrusion policies
- Implement management options for network security solutions (single vs. multidevice manager, in-band vs. out-of-band, cloud vs. on-premises)
- Configure AAA for device and network access such as TACACS+ and RADIUS
- Configure secure network management of perimeter security and infrastructure devices such as SNMPv3, NetConf, RestConf, APIs, secure syslog, and NTP with authentication
- Configure and verify site-to-site and remote access VPN
- Site-to-site VPN using Cisco routers and IOS
- Remote access VPN using Cisco AnyConnect Secure Mobility client
- Debug commands to view IPsec tunnel establishment and troubleshooting
- Security the Cloud
- Identify security solutions for cloud environments
- Public, private, hybrid, and community clouds
- Cloud service models: SaaS, PaaS, IaaS (NIST 800-145)
- Compare security responsibility for the different cloud service models
- Patch management in the cloud
- Security assessment in the cloud
- Describe the concept of DevSecOps (CI/CD pipeline, container orchestration, and secure software development)
- Implement application and data security in cloud environments
- Identify security capabilities, deployment models, and policy management to secure the cloud
- Configure cloud logging and monitoring methodologies
- Describe application and workload security concepts
- Identify security solutions for cloud environments
- Content Security
- Implement traffic redirection and capture methods for web proxy
- Describe web proxy identity and authentication including transparent user identification
- Compare the components, capabilities, and benefits of on-premises, hybrid, and cloudbased email and web solutions (Cisco Secure Email Gateway, Cisco Secure Email Cloud Gateway, and Cisco Secure Web Appliance)
- Configure and verify web and email security deployment methods to protect onpremises, hybrid, and remote users
- Configure and verify email security features such as SPAM filtering, antimalware filtering, DLP, blocklisting, and email encryption
- Configure and verify Cisco Umbrella Secure Internet Gateway and web security features such as blocklisting, URL filtering, malware scanning, URL categorization, web application filtering, and TLS decryption
- Describe the components, capabilities, and benefits of Cisco Umbrella
- Configure and verify web security controls on Cisco Umbrella (identities, URL content settings, destination lists, and reporting)
- Endpoint Protection and Detection
- Compare Endpoint Protection Platforms (EPP) and Endpoint Detection & Response (EDR) solutions
- Configure endpoint antimalware protection using Cisco Secure Endpoint
- Configure and verify outbreak control and quarantines to limit infection
- Describe justifications for endpoint-based security
- Describe the value of endpoint device management and asset inventory systems such as MDM
- Describe the uses and importance of a multifactor authentication (MFA) strategy
- Describe endpoint posture assessment solutions to ensure endpoint security
- Explain the importance of an endpoint patching strategy
- Secure Network Access, Visibility, and Enforcement
- Describe identity management and secure network access concepts such as guest services, profiling, posture assessment and BYOD
- Configure and verify network access control mechanisms such as 802.1X, MAB, WebAuth
- Describe network access with CoA
- Describe the benefits of device compliance and application control
- Explain exfiltration techniques (DNS tunneling, HTTPS, email, FTP/SSH/SCP/SFTP, ICMP, Messenger, IRC, NTP)
- Describe the benefits of network telemetry
- Describe the components, capabilities, and benefits of these security products and solutions
- a Cisco Secure Network Analytics
- b Cisco Secure Cloud Analytics
- .c Cisco pxGrid
- .d Cisco Umbrella Investigate
- .e Cisco Cognitive Intelligence
- f Cisco Encrypted Traffic Analytics
- g Cisco Secure Client Network Visibility Module (NVM)
- داشجویان کندو مشغول به کار شدن در...

فناوری اطلاعات شاتل

شرکت عالیفرد سنایچ

بانک پاسارگاد

بانک ملت

شرکت ارتباطات آسیاتک

پیشگامان توسعه ارتباطات

ایران خودرو

بانک خاورمیانه

ماموت خودرو

پارس خودرو
- اساتید این دوره
- نمونه تدریس
- نظرات شما